Data Immutability in Blockchain Network
Data Immutability is one of the key aspects of Blockchain Technology. In this article, I will explain the meaning of this term in the context of blockchain and how we achieve data immutability.
Blockchain is a popular platform because of the data security that such a type of architecture offers. Besides various features of blockchain technology, like decentralization and consensus mechanisms, blockchain has one more important feature. This crucial function is data immutability.
This article will discuss how blockchain network design helps achieve data immutability. We will also touch upon the data interoperability concept to enable future blockchain networks to communicate with each other.
What is Data Immutability?
Immutability means something permanent, and we cannot change it. Data Immutability in a blockchain refers to the extreme difficulty one will face in altering or changing the existing data in the blockchain.
Organizations employ various mechanisms ranging from access controls, multiple approvers, reconciliation, audit trails, and firewalls to ensure data immutability in databases.
Despite employing these means, data stored in the database is mutable. It means that people with enough access rights and authorization can alter the data after accessing it. This is where immutability in blockchain technology makes the biggest impact.
How Data Immutability Achieved in Blockchain?
Various technological aspects ensure the data immutability of a blockchain. These are the Hash function & checksums, decentralized consensus, economic incentives in some blockchain networks, and the overall data structure and data redundancy inside the network’s nodes.
Please read through for a detailed explanation of the above:
1. Cryptographic Hash Functions and Checksums:
Blockchain forms a chain of blocks connected via a link known as the previous hash pointer or simply the previous hash. The hash of a block is calculated for all the contents in the block header using a hashing algorithm.
The hash of each block includes the hash of the previous block. This creates a chain of blocks where each one is dependent on the previous. Any attempt to alter a block would require recalculating the hash for that block and all subsequent blocks.
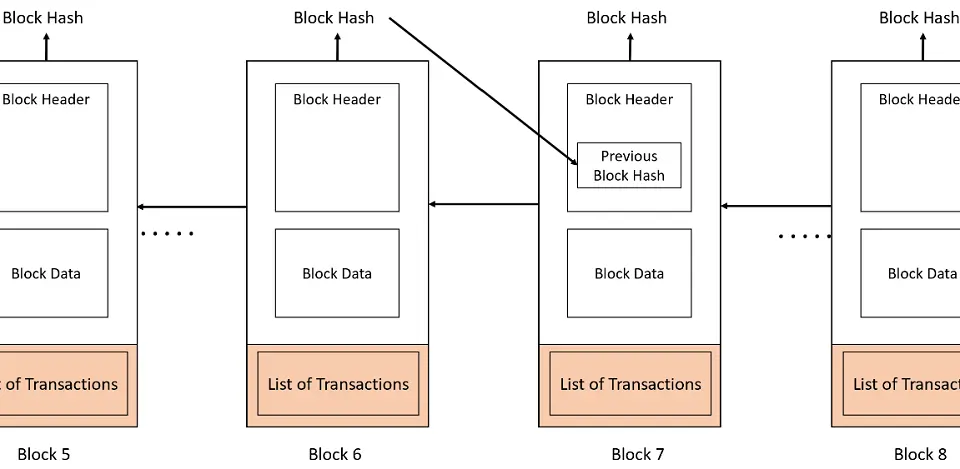
The above diagram shows the inclusion of the previous block’s hash in the second block. After this, the After this, the hash of the next new block is created, making the blockchain immutable.
The cryptographic hash function has a unique property: even a small change in the input data (e.g., a single transaction within a block) will produce a drastically different hash.
With any change in the hash of any block, the block next to it will no longer have a link to this block, as the previous hash will not match the new block. And any broken links between any two blocks will make the blocks invalid.
The Merkel root of the Merkel Tree is a part of the block header, and any change in any constituent blockchain transaction results in a change in the Merkel root. Hashing algorithms are deterministic, resulting in a different output if the input changes. Therefore, a change in the Merkel root will change the hash of the entire block.
Detailed Explanation of Hashing in Block Structure to Help in Immutability
Blockchain architecture makes the blockchain network immutable by design. There are core reasons behind blockchain networks achieving immutability, as discussed below:
Cryptographic Hashes are one of the key elements that make blockchain immutable. It is because we cannot reverse-engineer the hashes. The most popular hash function used in most blockchain networks is SHA-256, i.e., Secure hash Algorithm 256.
If we want to use an SHA-256 algorithm in Python, we must use the “hashlib” Python package.
Example of generating a hash Using Hashlib Function
Please refer to the following code:
import hashlib
hash = hashlib.sha256('Immutable Blockchain')
print(h.hexdigest())The SHA256 function generates a 64-character string irrespective of the length of the input text given. This fixed 64-character string is also known as a digital signature. Similarly, a block header hash is calculated as a double SHA 256 hash of all the block constituents.
Block header hash = SHA256 (SHA256 (previous block hash + Merkle root + timestamp + difficulty target + nonce))
Therefore, if there is a modification in the transaction, the modification will affect the transaction’s hash value, affecting the Merkle root. Moreover, since the Merkle root is one of the components of the block header, this will cause a ripple effect.
Moreover, this ripple effect will cause the block header hash to undergo modification. This would lead to a mismatch with the hash value of the next block. This is because the next block’s hash value depends on the current block’s hash value. Thus ultimately disrupting the chain of blocks.
That is why the immutability of the blockchain network increases with the increase in the number of blocks.
Checksum and Blockchain Immutability
Please note that the like hash of any block, checksum primarily designed for error-checking and error-detection, especially during data transmission, are the inputs to the next block. After this, the hash generation for the new block takes place. And the process continues.
Checksums also play a role in ensuring data immutability. However, while checksums can help verify data integrity and indicate tampering, they are only one piece of the puzzle when ensuring data immutability. The context in which they are used and the potential threats are crucial considerations when deciding the appropriate mechanisms to ensure data remains unchanged.
How Checksums in Data Integrity?
Data Integrity Verification:
- A checksum is a representation of data. If the data changes, the checksum will change.
- By calculating and storing a checksum alongside data, one can later verify that the data has not changed by recalculating it and comparing it to the stored value. If they match, the data remains unchanged. The data may have been altered or corrupted if they don’t match.
Tamper Evidence:
While checksums don’t inherently prevent tampering, they do provide evidence of tampering. An entity wishing to alter data maliciously must adjust the checksum to match the altered data. The mismatched checksum will signal the data alteration if they fail to do this.
Redundancy:
Multiple checksums or hashes may be used in some applications for added assurance. This redundancy can make undetected tampering even more unlikely.
Summary of Checksum and Data Integrity
To summarize, please note that the checksum algorithm ensures data integrity and identifies data transmission errors.
The difference in the cryptographic hash and checksum algorithm is as follows:
- A cryptographic hash protects against a motivated attacker.
- A checksum protects against accidental changes.
2. Decentralized Consensus
- The blockchains are decentralized. Therefore, no single party controls the blockchain network, making it difficult to make changes as power is distributed. Instead of a single entity validating transactions and adding blocks, multiple nodes (or participants) in the network do so. In such a distributed network, changes are not possible without a consensus.
- In proof-of-work systems like Bitcoin, for a block to be added to the blockchain, most nodes must agree (or reach a consensus) that the block is valid. This process requires solving a computationally intensive problem, which is a deterrent to malicious actors trying to alter the chain.
- Other consensus mechanisms like proof-of-stake, delegated proof-of-stake, and Byzantine fault tolerance also have their own ways of ensuring that participants agree on the state of the blockchain.
3. Economic Incentives:
- In many blockchain systems, participants (especially miners in proof-of-work systems) are rewarded for their efforts in validating and adding transactions to the blockchain.
- If a malicious actor wanted to alter the blockchain, they would need to command more computational power than the rest of the network combined (a 51% attack). This would be extremely costly, and, in most cases, the potential rewards of carrying out such an attack would be far less than the costs involved.
4. Data Structure and Redundancy:
- The blockchain’s structure inherently makes older blocks harder to change. As new blocks are added, the effort required to change older data and recalculate all subsequent blocks becomes prohibitive.
- Additionally, the blockchain is redundantly stored across many nodes in the network. This means that even if one or a few nodes were compromised, most nodes would still have the correct, unaltered version of the blockchain.
Challenges with Blockchain Data Immutability
There are typically two challenges that emerge with the evolution of technology. These challenges are 51 Percent Attack and Quantum Computing. Let’s understand how these two challenges can lead to compromising blockchain immutability.
51 Percent Attack
It is an attack when one individual or organization holds over 50 percent of computing power. This is quite difficult to achieve, especially for popular public blockchain networks such as Bitcoin, Ethereum, etc., as the network size is tremendous but never impossible. Such a computation can allow hackers to alter the transactions, compromising the blockchain’s immutability.
Quantum Computing
Harnessing the laws of quantum mechanics, quantum computing is becoming a rapidly growing technology that can solve issues that are too complex for traditional computers.
The objective is to increase the computing power of computers dramatically. There is a belief that quantum computing can reverse the hashing process to compromise the blockchain’s immutability.
Apart from Immutability, one more critical factor of interoperability makes blockchain future-ready.
Interoperability with Data Immutability for Blockchain’s Future
The interoperability of blockchains is one of the key features by which two different networks can communicate. Unfortunately, there is no mechanism today where two blockchains can communicate with each other.
However, having such a mechanism will increase the ability of blockchain technology to have more use cases and applications for blockchain technology.
Having such mechanisms in place will ensure the globalization of blockchain networks across the globe and will make blockchain technology production ready. Furthermore, Furthermore, with consistency in data across platforms, the possibilities of setting up a truly global network will be very high.
The cross-chain protocol ensures interoperability in the blockchain. Ripple is already in the early development stage as of 2022 to use cross-chain protocol and exchange information across multiple blockchains.
In addition, numerous blockchain projects such as Polkadot blockchain, Blocknet, Cosmos Blockchain, and a lot more are working to achieve the objective of interoperability in the blockchain.
The biggest issue in interoperability that I think of is establishing trust in a trustless (no single party controls the system) blockchain environment. How can a consensus be achieved if multiple blockchains interact with each other?
Summary
Blockchain is a highly secured network where transactions cannot be hacked. This happens because of the data immutability feature of the blockchain.
Immutability is an essential feature of the blockchain to prevent data manipulation and to help identify malicious nodes in the blockchain network. Therefore, data immutability is one of the biggest benefits of blockchain technology, that people can not alter or manipulate the transaction data after the conclusion of a transaction.
In this post, we have developed an understanding of data immutability in blockchain networks.
We further developed an understanding of the concept of interoperability and looked at some ongoing work to achieve interoperability in blockchain networks. We also discussed how immutability works in blockchain and the associated risks, namely, the 51 Percent attack or quantum computing threats to interoperability.

Tavish lives in Hyderabad, India, and works as a result-oriented data scientist specializing in improving the major key performance business indicators.
He understands how data can be used for business excellence and is a focused learner who enjoys sharing knowledge.
