Data Security: Importance, Spheres, and Best Practices

Data Security refers to practices employed in securing data from unauthorized tampering or corruption in an IT ecosystem. The entire digital world is run on data, and hence the statement, “data” is the new oil.”
Data is in files, databases, accounts, and networks in forms like emails, passwords, texts, names, IDs, or electronic cash. We need to ensure the security of all these items from threat or loss.
Effective data security practices revolve around sets of software, principles, controls, applications, and techniques that identify, store, maintain, and protect the datasets in the above-mentioned systems.
Why Data Security is Important
Virtually every day, sensitive data is lost or stolen around the world. This event is known as cyber theft. As a result, security practices and strategies need to be in place to mitigate cyber theft in different scenarios.
In Japan, for example, Mihoko Matsubara, chief cyber security strategist at NTT, released Japan’s Cyber Security Strategy for the Tokyo 2020 Olympic Games in defense of the recurring attacks by threat actors targeting athletes. A total of 450 million security events were blocked during the Games, including unauthorized communications to the official website.
Data is kept secure for a myriad of reasons. For example, companies and organizations keep sensitive data secure to protect their brand, intellectual capital, and customer information, provide critical infrastructure controls, etc.
Governments secure sensitive data to prevent the leakage and misuse of highly classified information. These data could be identities, text files, or assets to the nation that must not fall into the wrong hands.
Internet platforms serve as a sea of critical data such as credit card details, login credentials to important apps, digital identities, etc.
Bodies who offer the services mentioned above, or more, must take data security essential. Therefore, having a cyber-security strategy is an important step any start-up, government, or company must take.
A slight data breach can cause an overhaul: lost electronic cash, access to personal identity and digital assets, information leakage, etc.
Data Security practices and strategies are applied in the following systems and platforms:
Securing Data with Network and Endpoint Security

Please note that we have covered the subjects of Network security and Endpoint security in detail under another article, “What is IT Security.”
Data Privacy

Data privacy has become a key topic in digital discussions worldwide. It emphasizes protecting personal and sensitive information from unauthorized use.
Both big corporations and individual users are diving deeper into the digital world. Managing and protecting data carefully is becoming very important. This management is not just a legal need but also an ethical requirement.
Defining Data Privacy
Data privacy pertains to the right to autonomy and privacy over one’s personal information.
Data privacy involves practices, policies, and technologies to manage data collection, storage, processing, and sharing. Moreover, data privacy also involves discarding and deleting data to meet compliance requirements. Therefore, data privacy ensures judicious, safe, diligent, and secure data handling.
Vitality of Data Privacy
- Personal Autonomy: Individuals attain control over their personal information, dictating who has access to it and how it’s utilized.
- Trust and Reputation: For organizations, upholding data privacy means earning customer trust and fostering a reputable brand image.
- Regulatory Compliance: Adhering to global data protection laws and standards safeguards entities from legal issues and financial penalties.
Core Principles of Data Privacy
- Data Minimization: Collect only the data that is directly necessary for the intended purpose.
- Purpose Limitation: Use the data solely for the purpose for which we gathered it.
- Data Accuracy: Ensure the data is accurate, complete, and up-to-date.
- Security: Implement robust safeguards to protect data from unauthorized access and breaches.
- Accountability: Establish clear ownership and responsibility for data protection.
- Transparency: Clearly communicate how, why, and what data is being processed.
- Lawful Processing: Ensure that data handling adheres to applicable laws and statutes.
Challenges and Road Ahead
Despite stringent laws and advancements in security technologies, data privacy continues to grapple with challenges such as cybersecurity threats, technological advancements, and the global nature of the internet. The myriad of data privacy laws across different regions further complicates navigating the data privacy landscape.
With these challenges, organizations and people are shifting toward focusing more on privacy. This includes often checking systems and always being aware of data rules. Also, they’re adding technology solutions to ensure data privacy is a core part. This ensures it is part of all digital interactions..
As we sail further into the digital age, data privacy will persist as a pivotal focal point, shaping policies, influencing technologies, and steering ethical practices, thereby safeguarding our digital footprints while facilitating the seamless flow of information across the digital expanse.
The conversation about data privacy is sure to change and grow. It will become closely tied to our digital stories and tech improvements. This will create a future where protecting data and advancing technology go hand in hand smoothly.
Data Loss Prevention (DLP)

In an era where data reigns supreme, safeguarding it from accidental or intentional loss, leakage, and theft is paramount.
Data Loss Prevention (DLP) emerges as a critical framework, ensuring that unauthorized entities do not lose, misuse, or access sensitive or critical information.
DLP is a confluence of strategies, policies, and tools that aim to protect and secure data during its lifecycle – while in use, in motion, or at rest.
Understanding DLP
Data Loss Prevention (DLP) mainly works to find, watch, and shield data using set policy rules and clear identifiers. It aims to control and oversee how information is moved and used.
DLP sets limits or stops data transfers based on the company’s internal policies. Moreover, DLP also ensures that data transfers meet regulatory compliance needs.
Key Components of DLP
- Policy and Compliance Management: Crafting policies that identify what constitutes sensitive data and establishing guidelines for handling it.
- Data Identification and Classification: Determining and labeling data according to its sensitivity level or importance.
- Data Monitoring and Analysis: Continuously observing data transmission and use, ensuring policy compliance.
- Incident Response and Management: Detailing and responding to policy violation incidents, ensuring minimal damage and future prevention.
- User Activity Monitoring: Overseeing how users interact with sensitive data, ensuring no malevolent or non-compliant actions are taken.
Why DLP is Indispensable
- Regulatory Compliance: Adhering to data protection regulations and avoiding hefty fines.
- Protecting Intellectual Property: Safeguarding proprietary information from landing in the wrong hands.
- Preventing Data Breaches: Proactively securing sensitive data, thus shielding the organization from potential reputational damage.
- Ensuring Operational Continuity: To avoid disruptions from crucial data loss.
Challenges and Solutions in DLP Implementation
- Complexity in Data Identification: Understanding what data to protect can be intricate. Therefore, the solution is to employ automated data classification and use machine learning to identify and tag sensitive data.
- Policy Management: Defining policies that are thorough yet not obstructive can be a delicate balance. Solution: Regularly reviewing and refining policies with stakeholder input and technological advancements.
- User Adoption: Resistance or ignorance towards DLP policies can hinder effectiveness. Solution: Conducting regular training and making users aware of the importance and functioning of DLP.
Navigating Through the Future with DLP
As technology evolves, so does the sophistication of threats that illicitly harness data. In this context, DLP will continue to evolve, intertwining advanced technologies such as Artificial Intelligence and Machine Learning to enhance its effectiveness in safeguarding data against internal and external threats.
We live in a digital age full of data. Data Loss Prevention (DLP) acts like a careful guard in this environment. It carefully protects data from unwanted actions and keeps it safe. Therefore, a company’s digital assets are always protected. This follows a path of compliance and safe operation.
Consequently, DLP does not merely function as a technological tool. It evolves as a vital cog in an organization’s holistic strategy. This strategy encompasses both data governance and security aspects.
Data Security on Cloud Platforms

Cloud technology exists due to the need to make data, software, and other relevant products available globally. At the very heart of cloud platforms are data centers that are equally susceptible to breaches in security like their local counterparts.
Consequently, there exist security practices aimed at keeping cloud-based data systems safe. These include:
- Building a secure architecture
- Enforcing compliance
- Monitoring cloud networks and systems
- Using reliable authentication protocols
Hardware Modules and Virtualization
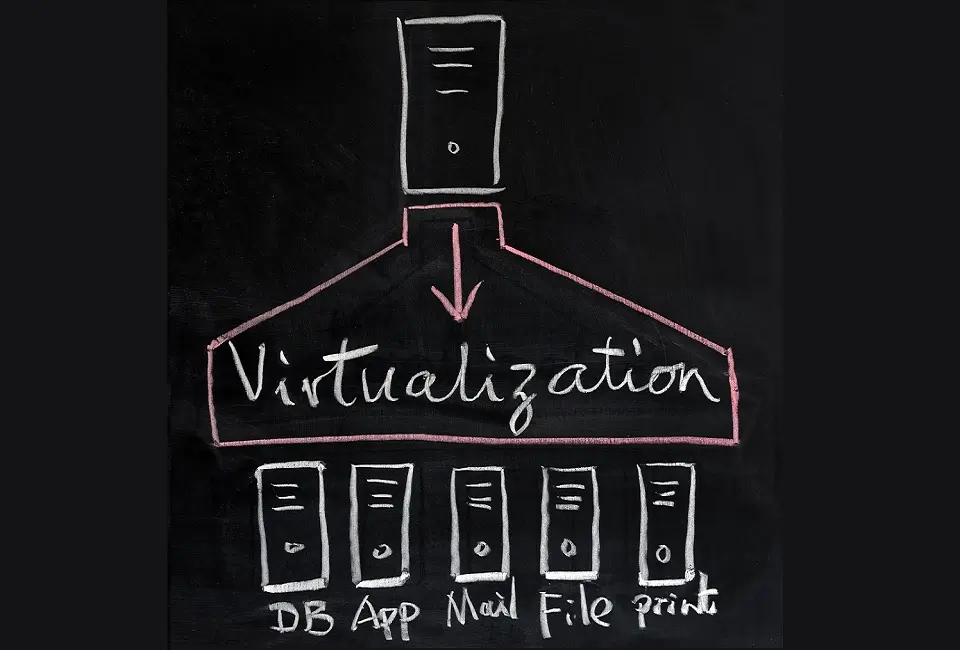
Understandably, data is as intangible as software. However, it is stored in hardware modules. Examples of these modules include memory chips and drives. Keeping these hardware modules from physically unwanted access is just as important as protecting their intangible data.
Moreover, hardware security may also entail several tools and devices that could be used for vulnerability protection. Examples are hardware firewalls, proxy servers, and devices that scan system ports or monitor network traffic.
Virtualization
Virtualization can play a crucial role in enhancing data security in various ways. When implemented and managed correctly, virtualization can provide additional layers of security and support various strategies to protect data and other IT assets. Here’s how:
1. Isolation of Applications
- Security through Segregation: Virtualization allows different applications and processes to be isolated from each other within separate virtual environments.
- Minimizing Risks: If one virtual machine (VM) is compromised, the threat is contained and doesn’t automatically spread to other VMs.
2. Simplified Data Management
- Centralized Management: Managing data and security configurations can be centralized, making it easier to enforce security policies consistently.
- Snapshot and Rollback: VMs can be snapshotted and rolled back to previous states, which can be vital after a malware attack or data corruption.
3. Secure Testing Environments
- Safe Testing: Virtualized environments allow organizations to create secure, isolated areas for testing and development without risking the main infrastructure.
- Malware Analysis: Security teams can safely study malware and cyber-attacks in isolated VMs without risking the broader network.
4. Enhanced Data Mobility
- Secure Data Transfers: Data can be moved securely between virtual environments, reducing the risk of exposure during transit.
- Data Encryption: Virtualized environments can implement robust encryption to protect data at rest and in motion.
5. Efficient Patching and Updating
- Non-Disruptive Updates: VMs can often be patched and updated with minimal disruption to the operational environment.
- Reduced Downtime: Through techniques like live migration, virtualization can limit downtime, ensuring continuous data availability and integrity.
6. Business Continuity and Disaster Recovery
- Rapid Recovery: Virtualization supports rapid recovery from failures and facilitates efficient data backup strategies.
- Business Continuity: Creating replicas of virtual environments ensures that services can be quickly restored in the event of a catastrophe.
7. Virtualization and Network Security
- Virtual Firewalls: Virtualization allows for the implementation of virtual firewalls that protect VMs and network segments.
- Micro-Segmentation: Enforcing network segmentation within the virtual environment can further contain threats and protect data.
Virtualization: Challenges and Considerations
While virtualization does provide various security advantages, it’s essential to acknowledge and address potential challenges:
- Hypervisor Vulnerabilities: The hypervisor, responsible for managing VMs, can be a target for cyber attackers and needs to be securely configured and regularly updated.
- Resource Allocation: Ensuring adequate resource allocation to prevent performance issues while maintaining security controls is vital.
- Secure Configuration: Like any technology, secure deployment and configuration of virtual environments are paramount to leverage security benefits.
In summary, while virtualization bolsters data security, its effective implementation and continuous management are vital to ensure its capabilities are fully leveraged securely.
Electronics Cash and Payment Systems

The evolution of digital technology has reshaped how transactions are conducted, bringing forth the proliferation of electronic cash and payment systems. While this digital transformation has significantly enhanced convenience and global connectivity in transactions, it has also introduced myriad challenges, particularly in securing financial data and safeguarding the integrity of these systems.
Pivotal Role of Security for Fintech
Security in electronic cash and payment systems is paramount. Financial transactions inherently involve sensitive data, such as user identification, bank details, and transaction histories, which are lucrative targets for malicious actors. Thus, ensuring that these details remain confidential and secure from unauthorized access and fraudulent activities is crucial.
Security Digital Payment Framework
A robust security framework for electronic cash and payment systems encompasses several components:
- Authentication: Verifying the identity of users to prevent unauthorized access.
- Authorization: Ensuring that a user has permission to perform a transaction.
- Encryption: Masking data to protect it during transmission across networks.
- Fraud Detection: Utilizing algorithms and monitoring tools to detect anomalous activities that may indicate fraudulent transactions.
Multifactor Authentication (MFA)
Implementing MFA adds a layer of security. It requires users to validate their identity using two or more verification methods – something they know (like a password), something they have (like a smartphone), or something they are (like a fingerprint). MFA significantly diminishes the likelihood of unauthorized access, even when user data is compromised.
Secure Socket Layer (SSL) Encryption
SSL encryption is pivotal in safeguarding data transmitted across networks. It ensures that data exchanged between users and electronic payment systems, such as credit card numbers or bank account details, is encrypted and secure from potential eavesdroppers.
Digital Payments: Compliance and Regulations
Compliance with regional and international data protection and payment processing regulations, such as the Payment Card Industry Data Security Standard (PCI DSS), is vital. These regulations stipulate mandatory protocols and practices that safeguard consumer data and ensure secure transaction environments.
Challenges and Future Considerations
Despite advancements in security technologies, the escalating sophistication of cyber threats poses ongoing challenges.
Phishing attacks, data breaches, and other fraudulent activities are persistent threats to electronic payment systems. Consequently, the continual evolution of security practices, technological enhancements, and adherence to emerging regulations are indispensable to maintaining the integrity of electronic cash and payment systems.
In summary, while electronic cash and payment systems have bolstered convenience and globalized economic activity, the onus of maintaining stringent, adaptable, and resilient security practices is crucial to safeguarding financial data and ensuring consumer trust in the digital transaction ecosystem.
Database Systems

Databases are records of identities, transactions, actions, monetary value, etc. They are equally important because they contain valuable information that must not fall into the wrong hands.
In database systems, SQL injection attacks are the most common. Other frequently reported attacks include Buffer overflow vulnerability, the dreaded DoS attacks, Privilege escalation, and Weak authentication.
Consequently, some best practices for keeping databases secure include the following:
- Creating database servers separate from others
- Using firewalls to protect databases, which system or database administrators manage.
- Constantly monitoring database activity either by using locks for database server rooms or setting up CCTV cameras
- Encrypting and backing up the data
- Frequently testing database security
- Using reliable authentication services
Big Data and IoT Data Protection

The Internet of Things is known for the generation of Big Data. Whether these data are stored in a data lake, cloud, or a local database, their networks or storage devices can be intercepted by malicious hackers to exploit the systems.
Research by Palo Alto Networks found that as much as 57% of IoT devices are vulnerable to medium- or high-severity attacks.
Security for IoT devices needs strong enforcement. One method is splitting the network for appliances and data-focused devices. It’s important to run hardware and software updates regularly. Using trustworthy identity and access management systems is also crucial.
Data Encryption
Navigating through the boundless digital universe, the protection of data becomes paramount. This is crucial both in transit and at rest to ensure privacy and confidentiality.
Encryption emerges as an invaluable safeguard in this context. It encodes information so that only authorized parties can access it. In essence, encryption translates the original data into an alternate form. Usually, this takes the form of a code. This code shields the data from unauthorized or unintended users.
The Essence of Encryption
- Cipher: A specialized algorithm to convert accessible data (plain text) into an unreadable form (cipher text).
- Key: A secret piece of information used for deciphering the encrypted data back to its original form.
In encrypted data, the original text, known as “plaintext,” is transformed into “ciphertext” using an encryption algorithm and an encryption key. When this data needs to be read, it is decrypted using a decryption algorithm and a decryption key.
Types of Encryption
- Symmetric Encryption: Utilizes the same key for data encryption and decryption. Though efficient, its key management and distribution can be complex in large-scale environments.
- Asymmetric Encryption: Uses two different keys – a public key for encryption and a private key for decryption. This method addresses key distribution issues but is computationally heavier than symmetric encryption.
Implementing Encryption Across Platforms
- Data Encryption: Securing data, whether at rest, in use, or in transit, to safeguard it from unauthorized access.
- End-to-End Encryption: Ensuring the encryption of the data on the sender’s system or device so that only the recipient can decrypt it.
- Email Encryption: Protecting the content of email messages to prevent entities other than the intended recipients from reading them.
- Disk Encryption: Encrypting the entire hard drive so that even the stored data is encrypted.
Significance of Encryption
- Data Security: Safeguarding data from unauthorized access during transmission and when stored.
- Regulatory Compliance: Ensuring adherence to various data protection regulations by protecting consumer information.
- Protecting Information: Guarding sensitive and proprietary information from potential cyber threats.
- Secure Communication: Enabling safe communication over insecure networks like the Internet.
Challenges Encountered
- Key Management: Safeguarding and managing encryption keys without compromising their security.
- Performance Overhead: Addressing the additional computational load that encryption can introduce.
- Complexity: Ensuring user-friendliness and simplicity while implementing robust encryption strategies.
Encryption: A Shield in the Cyber Realm
In today’s digital world, data moves freely and exists in many forms. Encryption acts like a strong wall, protecting data from unwanted access. It ensures that even if data theft occurs, it can’t be understood or used. It’s more than just a tool – it’s a need. In our increasingly online world, encryption quietly keeps data safe from hidden dangers in the vast online space.
Data breaches and cyber threats are becoming more advanced. Therefore, the role of encryption is becoming more important. It will keep evolving and become crucial to every piece of data. Encryption provides a security blanket for data. It protects data from ongoing threats trying to exploit weak spots.
Data Backup and Recovery

In the digital world, data is an extremely valuable asset. Protecting it from unexpected issues and cyber threats is crucial. Therefore, backup and recovery systems become crucial in this context. They provide strong protection by carefully saving data. This ensures data is available even when unexpected data loss happens.
Backup: An Essential Safety Net for Data
- Definition: Backup involves creating copies of data to protect against potential loss, corruption, or breaches.
- Forms of Backup:
- Full Backup: Copying every bit of data in the entirety of the digital environment.
- Incremental Backup: Storing data that has altered since the last backup, reducing data volume and time.
- Differential Backup: Backing up all changes made since the last full backup.
- Storage Solutions: This may involve on-premises storage, cloud-based solutions, or a hybrid model aligning with the organization’s needs and scale.
Recovery: The Revival from Data Setbacks
- Definition: Recovery entails restoring data from backup storage to its original location or an alternative location in case of data loss.
- Recovery Objectives:
- Recovery Point Objective (RPO): Identifies the maximum targeted period in which data might be lost from an IT service due to a major incident.
- Recovery Time Objective (RTO): Defines the targeted duration for restoring a business process after a disruption.
- Recovery Strategies:
- Data Retrieval: Reinstating data from the backup storage to its original or alternate location.
- System Restoration: Involves reinstating system operations and capabilities using the recovered data.
The Significance of Backup and Recovery
- Business Continuity: Ensuring businesses and organizations can maintain or swiftly resume essential functions following data loss.
- Data Integrity: Upholding the accuracy and consistency of data in the face of unexpected incidents, such as cyberattacks, hardware failures, or human error.
- Compliance: Adhering to regulatory demands about data preservation, security, and privacy.
Challenges and Considerations
- Data Growth: Navigating through the sheer volume and diversity of data to be backed up.
- Security: Ensuring the backup data is shielded from unauthorized access and cyber threats.
- Cost Management: Balancing between optimizing backup and recovery systems and managing expenditures.
Strategic Approaches to Backup and Recovery
- Automated Backups: Employing automated tools to execute backup tasks, reducing manual intervention and enhancing reliability.
- Periodic Testing: Regularly testing recovery plans to ensure efficiency and readiness in real-world scenarios.
- Data Classification: Prioritizing data based on criticality and determining backup frequencies accordingly.
DRR: The Pillar of Reliability in a Digital Ecosystem
Data backup and recovery strategies operate as the silent sentinels in the digital ecosystem, consistently assuring that despite uncertainties and adversities, data remains protected, recoverable, and perpetually available to uphold continuous business operations.
Backup and recovery systems are more than just technological tools. They also embody a promise of resilience and ongoing stability. This promise stands even during unexpected troubles. Therefore, creating a detailed and strong backup and recovery plan is vital. It helps navigate our digital world, protecting and recovering data during potential online troubles.
Web App and Mobile App Security

The internet is virtually home to billions of devices interacting with websites. Given this fact, web applications are easily the major prey for today’s threat actors. Using SSL for web data encryption and authentication is a primary way to keep apps secure.
Furthermore, the OWASP (embed link: https://owasp.org/Top10/) body annually updates the Top 10 vulnerabilities in web apps.
Similarly, mobile applications also see more security attacks. For example, hacking of game apps takes place quite often. Some modified clones of apps support in-app purchases, and fintech applications are easily overridden if they lack standard security features.
To keep mobile apps more secure, developers are advised to:
- Write secure code
- Encrypt data collected by the app with the best Cryptographic techniques
- Test software before pushing it to production, then actively hunt and eliminate bugs
- Use reliable authentication services
- Use only authorized APIs
- Deploy proper Session Management
Email Communication Security

Email is a preferred means of communication today, especially in the corporate world. Moreover, the majority of phishing attacks come in the form of emails.
As such, emails contain very sensitive data or are the authentication keys to sensitive data, whether corporate communications, payment services, or other sensitive data management systems related to consumers via emails.
Identity and Access Management (IAM)

In the digital world, countless interactions and transactions happen all the time. Safeguarding and managing user identities is crucial.
Identity and Access Management (IAM) become a key area in data security. It carefully manages identities and access within a network or system. IAM is not just a technology on its own.
IAM combines practices, policies, and tools. It ensures the correct people access the right resources. And it ensures this access happens at the right times and for the right reasons.
Why IAM Matters
IAM has two main jobs: it ensures real users can easily access what they need. At the same time, it keeps out unauthorized access and potential breaches. It handles digital identities and keeps them safe. This involves managing the link between user identities and their access levels. So, it balances making things easy for users and keeping everything secure.
Components of IAM
- User Identity Management: Administering a system’s creation, removal, and management of user identities.
- Authentication: Verifying the user’s identity, ensuring that the individual or system is who it claims to be.
- Authorization: Determining whether a user should have access to a specific resource.
- Single Sign-On (SSO): Enabling users to access multiple applications or services with a single set of credentials.
- Multi-Factor Authentication (MFA): Adding an extra layer of security by requiring multiple forms of identity verification.
- Access Control: Mechanisms that determine and enforce what resources a user can access.
- Audit and Compliance: Monitoring, logging, and reporting accesses and modifications for compliance and investigative purposes.
IAM in the Modern Landscape
Cloud services and remote work are now common, so IAM has changed to fit different user environments. The main method is simple but important: check the user’s identity, then give access as needed. IAM helps provide safe user experiences and meet regulatory rules. It has become a crucial part of modern IT security.
In contemporary digital infrastructures, IAM goes beyond access management, venturing into cybersecurity, user experience, and regulatory compliance.
IAM ensures the organization’s digital avenues remain secure yet accessible, optimizing operational efficacy while minimizing risk. Consequently, IAM has become an indispensable protagonist in the narrative of data security, safeguarding identities and access amidst the expansive and intricate digital landscape.
Incident Response Plan
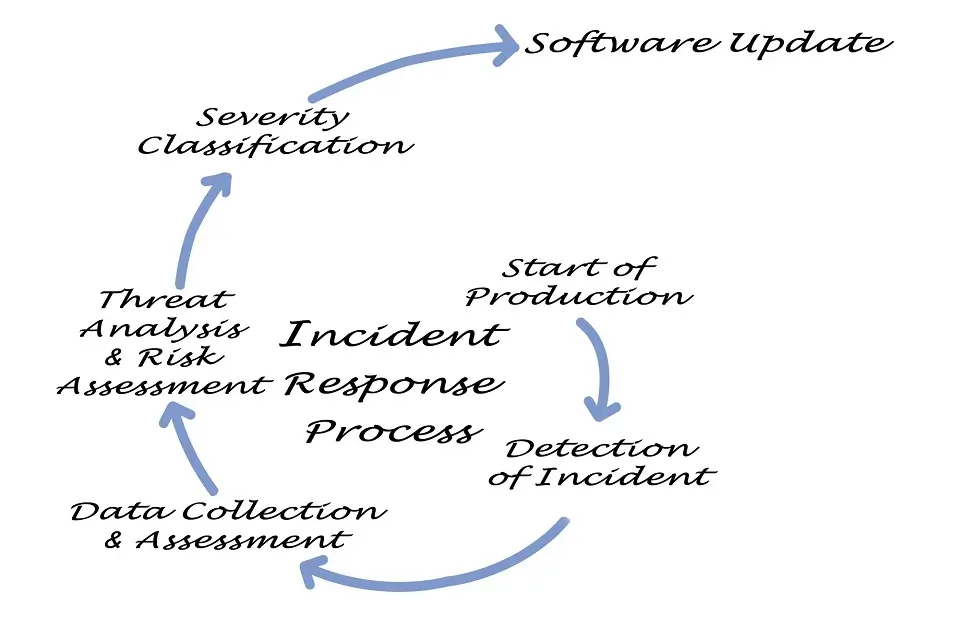
In the volatile digital world, where cybersecurity threats constantly loom, the Incident Response Plan (IRP) emerges as a crucial, strategic blueprint. It is meticulously designed to manage and mitigate the consequences of a cybersecurity incident, thereby safeguarding organizational integrity and minimizing recovery time and costs.
Defining Incident Response
- Concept: An incident response plan involves a well-orchestrated approach detailing the processes to follow when a cybersecurity incident occurs.
- Incidents: These can range from a data breach advanced persistent threat to an insider attack.
- Objective: To handle the situation to limit damage and reduce recovery time and costs, preventing future incidents.
Key Components of an Incident Response Plan
- Preparation: Developing and establishing an IRP, including creating an incident response team and equipping them with the necessary tools and resources.
- Detection and Identification: Utilizing technologies and strategies to identify cybersecurity incidents promptly.
- Containment: Implementing measures to contain the incident and prevent further damage, both in the short term and long term.
- Eradication: Once contained, eliminate the root cause of the incident.
- Recovery: Restoring and validating system functionality for business operations and monitoring for signs of weaknesses to prevent further exploitation.
- Lessons Learned: Analyzing the incident and the effectiveness of the IRP, including what worked well and what did not, and updating the plan accordingly.
Roles in Incident Response Team
- Incident Response Manager: Orchestrates the response, ensuring each role is clear and that team members perform their tasks efficiently.
- Security Analyst: Investigates and analyzes the incident, determining how it occurred and its impact.
- IT Professional: Focuses on managing the technical aspects of containment and eradication.
- Legal Advisor: Provides advice on legal and compliance issues and communicates with regulatory bodies.
- PR and Communication Expert: Manages communication internally and externally to control the narrative and maintain trust.
Incident Response Strategy
- Anticipate and Prepare: Constantly anticipate potential threats and ensure the organization’s adequate preparation to address them.
- Comprehensive Analysis: Involves thorough investigation and documentation of incidents from identification to resolution.
- Collaboration: Engage various departments to create a comprehensive and collaborative IRP.
- Continuous Improvement: Regularly test and refine the IRP, adapting to new threats and utilizing insights from past incidents.
Cruciality of a Robust IRP
- Minimize Impact: Quickly contain and mitigate incidents to minimize financial and reputational impact.
- Regulatory Compliance: Ensure alignment with regulatory requirements regarding data breaches and notifications.
- Safeguard Reputation: Maintain customer trust by demonstrating preparedness and transparency during and after an incident.
- Enhanced Security Posture: Strengthen the organization’s overall cybersecurity posture by learning and evolving from each incident.
Incident Response: Conclusion
In the digital world’s battlefield, the Incident Response Plan acts as a protective shield for organizations. It’s carefully made to protect and change in response to cybersecurity incidents. It’s not just a reactive tool but also a constantly evolving process.
Incident Response Plan learns, adapts, and strengthens defenses against ever-changing cyber threats. Therefore, creating, improving, and using a strong, flexible IRP is very important. It ensures survival and a strong and safe ongoing journey among constant cyber dangers.
Compliance and Data Protection Law

Digitalization touches every part of our modern life. So, the need for data protection and following rules grows a lot. It turns into a basic pillar for businesses and digital platforms.
Going through the detailed and different world of data protection law needs careful understanding. Moreover, it requires strategic planning and a solid use of the best practices. This helps to keep both user data and the organization safe and sound.
Intersecting Paths of Compliance and Data Protection
- Compliance: Adhering to a set of specified rules, which could be legal, regulatory, or policy-driven, that organizations must follow.
- Data Protection: Implementing policies, technologies, and practices that aim to safeguard data from unauthorized access, disclosure, alteration, or destruction.
The Essence of Data Protection Law
Data Protection Laws, differing but sharing commonalities across various geographical jurisdictions, are crafted to:
- Safeguard Privacy: Protect individuals’ privacy against unauthorized data access and handling.
- Ensure Transparency: Mandate organizations to be transparent about how and why data is processed.
- Uphold Rights: Establish and protect the rights of individuals concerning their personal data.
- Instill Accountability: Ensure entities that handle data are accountable for its protection and compliant use.
Data Compliance in Varied Jurisdictions
Navigating through compliance is complex, primarily when organizations operate globally, subjecting them to various international and local data protection laws, including:
- GDPR (General Data Protection Regulation) in the European Union safeguarding data and privacy of EU citizens.
- CCPA (California Consumer Privacy Act) in the United States, empowering California residents with specified data protection rights.
- PDPA (Personal Data Protection Act) in various Asian countries, each with its particular frameworks and regulations.
Achieving and Maintaining Compliance: A Strategic Undertaking
- Understanding Regulations: Comprehend the specific requirements of all applicable data protection laws and regulations.
- Data Mapping: Understand what data is collected, stored, and processed to ensure thorough protection and compliance.
- Implementing Safeguards: Employ technological and procedural safeguards to protect data from breaches and unauthorized access.
- Ensuring Transparency: Be clear and transparent with stakeholders, especially data subjects, about data usage policies.
- Regular Audits and Assessments: Conduct routine checks to ensure all data protection and compliance mechanisms are effectively operational.
- Training and Awareness: Cultivate a culture of data protection awareness among employees and stakeholders.
Challenges and Solutions in Compliance and Data Protection
- Global Operations: Navigating through varied and sometimes conflicting international data protection laws is challenging. A unified, stringent data protection policy often proves beneficial.
- Technological Evolution: With technological advancements, new avenues of data vulnerabilities emerge. A continuous evaluation and adaptation of data protection strategies are paramount.
- User Trust: Consistently assures users their data is protected and transparently communicates data usage policies to maintain trust.
Future Trends and Forward Paths
- Global Harmonization: Efforts towards more harmonized global data protection standards are evident and will likely continue.
- AI and Data Protection: Integrating AI into data protection while ensuring ethical use and compliance will be a crucial focal point.
- Consumer Awareness: As consumers become more data-aware, their expectations for stringent data protection will rise, impacting regulations and compliance norms.
Data Protection: Concluding Notes
Navigating through compliance and data protection law is an ever-evolving journey.
This evolving journey for compliance is because of technological advancements and regulatory changes. Shifting user expectations also play a significant role in this journey.
A proactive, informed, and adaptive approach is crucial in this navigation. This approach safeguards both organizational and user data. Moreover, it ensures the sustained trust of all stakeholders.
Data protection compliances also adhere to the regulatory tapestry enveloping the digital world. Balancing technological adoption with ethical data usage is vital. This balance will remain a cardinal endeavor in the ongoing digital journey.
Data Security Best Practices
General data security practices include encryption, hashing, tokenization, and important data management practices that protect data across all applications and platforms.
Below a list of “Best Practices” for protecting your personal and company data are given:
- Understand how databases work and how to keep them secure
- Recognize sensitive data
- Enforce control over access to data – physically, technically, and administratively.
- Use data encryption works
- Back up data regularly
- Use RAID for servers
- Use cluttering and load balancers for multiple systems
- Harden your systems, i.e., Operating Systems, email servers, FTP servers, and web servers.
- Use trusted security software like antivirus software, firewalls, IDSs, etc.
- Perform vulnerability assessments and cybersecurity penetration tests
Conclusion
As mentioned earlier, data security is important to the IT ecosystem. Data is generated as output as companies, governments, and individuals put their marks in the digital sand.
Security engineers and occupants of similar roles protect sensitive and important data from potential threats. While there are no rigid rules, this article provides general best practices that can be applied to different spheres of the IT ecosystem.

MacBobby Chibuzor is a Robotics Hardware Engineer and a Tech Polyglot. He also has practical experience in Software Engineering and Machine Learning, with an interest in embedded systems and Blockchain technology. In addition, Mac loves to spend his free time in technical writing.
